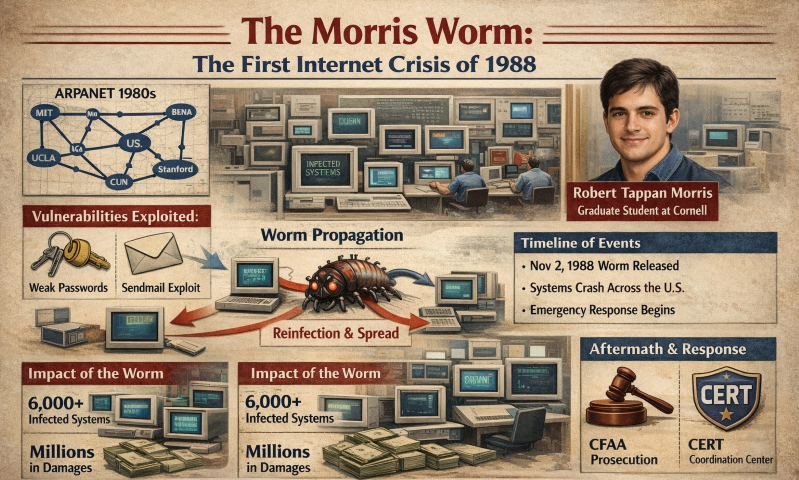
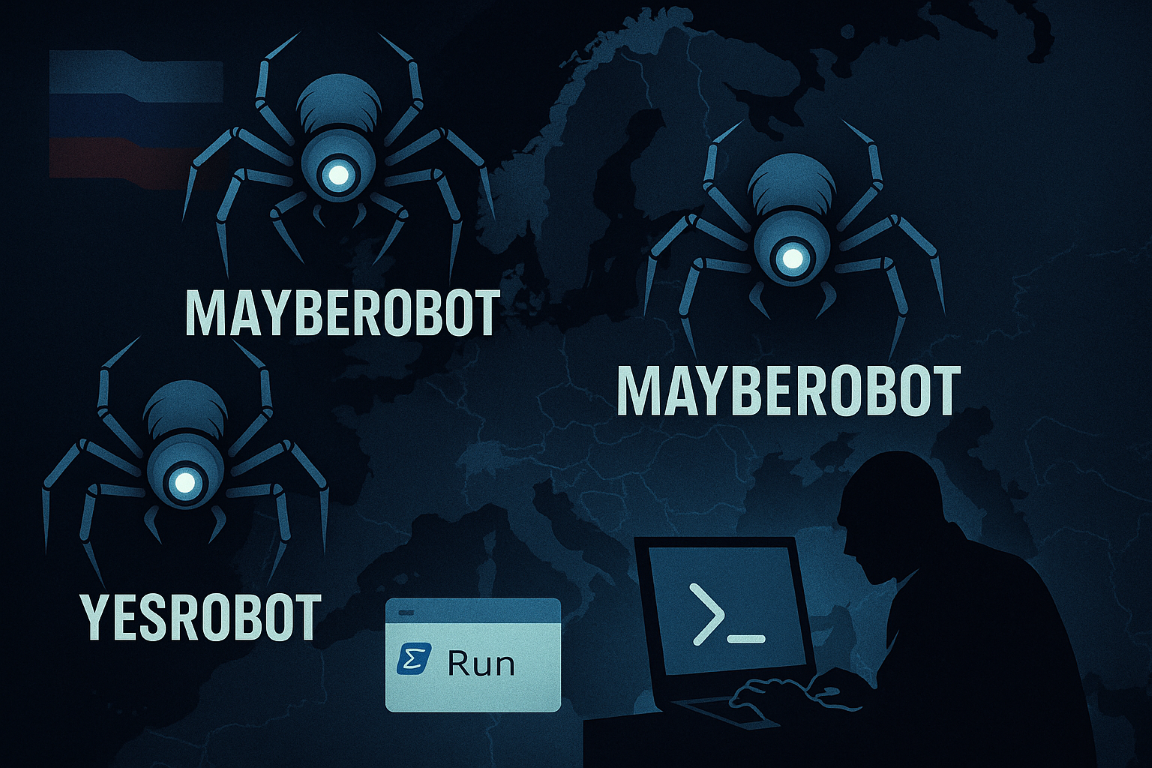
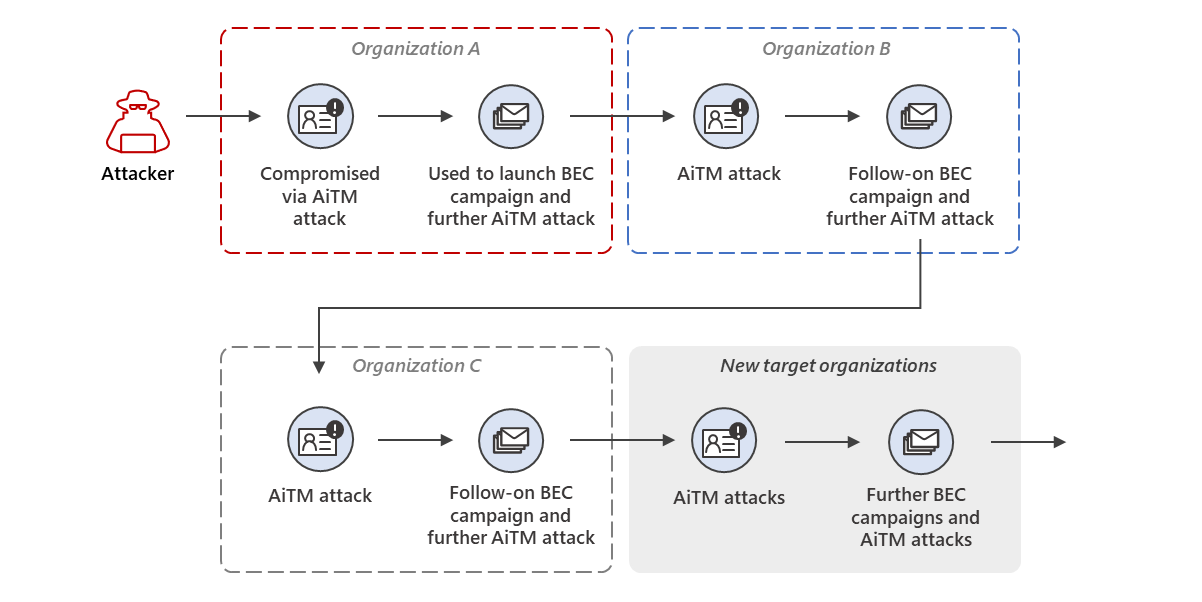
Popular News

India May Fast-Track Big Tech Compliance Under Data...
- BY Aayushman Verma
- January 22, 2026

Fast Flux Botnets Unmasked: Inside the Resilient Infrastructure...
- BY Shubhendu Sen
- January 22, 2026


Whisper-Pair Exposed: How a Flawed Google Fast Pair...
- BY Vinay Pratap Singh Bhadouriya
- January 22, 2026
Cyber & Tech Updates →
Trending →
Understanding the Recent Instagram Data Incident and How Scraping Works
- BY Shubhendu Sen
- January 12, 2026
Cyber Weekly
HAND-PICKED
Crime & Fraud
Tech Updates
Scaling Potential: Google bets big on Indian A.I Startups
- January 18, 2026
Apple Partners With Google Gemini to Power Next-Generation AI Siri
- January 15, 2026
Blogs
HAND-PICKED
Editor's Choice
Fake ‘Digital Arrest’ Scams on the Rise, CM
- BY Shubhendu Sen
- January 5, 2026
Google Uncovers Three New COLDRIVER Malware Families —
- BY Shubhendu Sen
- October 21, 2025