Introduction
Security researchers have attributed a sophisticated, financially motivated campaign to a threat actor tracked as UNC5142 that blends classic web compromise techniques with novel blockchain-based obfuscation. By embedding multi-stage JavaScript into vulnerable WordPress instances and outsourcing key pieces of the infection chain to smart contracts on BNB Smart Chain (BSC), UNC5142 has distributed multiple information-stealer families — including Atomic (AMOS), Lumma, Rhadamanthys (RADTHIEF), and Vidar — against both Windows and macOS targets.
Background / Context
The campaign leverages two core enablers:
- Compromised WordPress sites — attackers inject malicious JavaScript into plugin and theme files, and in some cases directly into WordPress databases, giving the malware a high-volume distribution platform.
- “EtherHiding” (blockchain-hosted data) — malicious actors store or reference encrypted landing pages and runtime parameters in smart contracts on public blockchains (notably BNB Smart Chain) to hide payload metadata and make takedown more difficult.
This technique was first publicly documented in 2023 and has since evolved: Google Threat Intelligence Group (GTIG) has observed the actor scale to thousands of infected pages and refine its smart-contract architecture for greater agility.
Technical Details
Multi-stage infection via CLEARSHORT
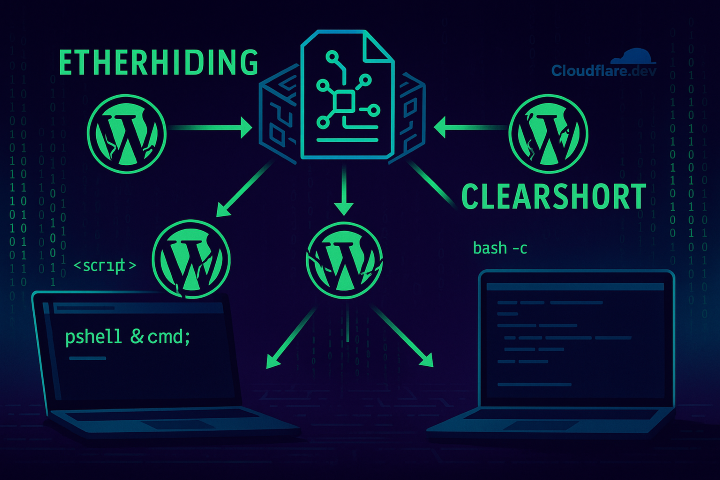
At the heart of UNC5142’s flow is a multi-stage JavaScript downloader identified as CLEARSHORT (a ClearFake variant). The sequence typically follows:
- Stage 1 — Malicious JavaScript injection: Injected into plugin/theme files or the WordPress database; this small script queries a smart contract on BSC.
- Smart contract retrieval: The contract contains or references encrypted landing-page payloads (a landing page or decryption key) hosted externally.
- Landing page / ClickFix social engineering: The landing page (often hosted under Cloudflare
.dev) uses ClickFix lures to trick users into executing commands in Windows Run or macOS Terminal, which downloads and runs additional scripts. - Final payload execution: On Windows the flow frequently downloads an HTA from MediaFire, which executes a PowerShell loader that fetches an encrypted final payload (from GitHub, MediaFire, or the actor’s infra) and runs the stealer in memory to evade disk-based detection. On macOS, a curl-retrieved shell script delivers Atomic Stealer.
Smart contract architecture and operational agility
UNC5142’s infrastructure has evolved from a single-contract design to a proxy-inspired Router–Logic–Storage architecture. This mirrors legitimate upgradable-contract patterns and allows operators to change critical runtime data (landing page URLs, decryption keys) without updating JavaScript on compromised sites. Such changes cost a fraction of a dollar in on-chain gas fees but provide outsized operational flexibility and takedown resistance.
Infrastructure footprints
GTIG identified two parallel smart-contract infrastructures used in these campaigns:
- Main infrastructure — created in late November 2024 and continuously updated; the primary campaign backbone.
- Secondary infrastructure — funded in February 2025 as a tactical or surge-capacity deployment for testing new lures or enhancing resilience.
Both infrastructures play roles in delivery, rapid updates, and load distribution.
Timeline of Events
- July 2023 — ClearFake frameworks are first noted in the wild as drive-by download frameworks.
- October 2023 — EtherHiding tactics using Binance Smart Chain contracts are publicly reported.
- May 2024 — ClickFix social-engineering lures start to appear alongside ClearFake variants.
- November 24, 2024 — Main contract infrastructure deployed by UNC5142 (per GTIG analysis).
- December 2024 — Landing pages start serving encrypted payloads more consistently.
- February 18, 2025 — Secondary smart-contract infrastructure is funded.
- June 2025 — GTIG flags ~14,000 pages with injected JavaScript exhibiting UNC5142 behavior.
- July 23, 2025 — Last observed UNC5142 activity noted by GTIG; may indicate pause or operational pivot.
Related Incidents and Attribution
CLEARSHORT is assessed as a variant of ClearFake, previously analyzed in depth by third-party researchers. UNC5142’s use of Web3 primitives to host or reference payloads is consistent with previously observed EtherHiding cases and other campaigns that exploit distributed ledgers for resiliency and obfuscation.
Impact / Scope
- High scale: Tens of thousands of compromised pages provide a broad attack surface and high hit-rate potential.
- Cross-platform reach: Delivery chains target both Windows and macOS endpoints.
- Operational resilience: On-chain storage of landing-page parameters and frequent contract updates make takedowns and static detection more difficult.
- Stealthy execution: In-memory execution and encrypted payload delivery increase chances of evasion from conventional endpoint defenses.
Response / Mitigation
Site owners and administrators should prioritize:
- Performing immediate integrity checks of WordPress plugin and theme files and scanning the database for unauthorized script injections.
- Applying security updates to WordPress core, themes, and plugins, and removing unused or out-of-date components.
- Implementing strict file monitoring and integrity-checking solutions to detect unexpected changes.
- Hardened administrative access: enforce MFA, rotate credentials, and audit admin users.
Network and platform defenders should:
- Monitor for anomalous JavaScript loaders, especially scripts communicating with BSC addresses or unusual external domains (Cloudflare
.devpages, MediaFire, GitHub raw content URLs). - Block or closely inspect downloads from known hosting services used in these campaigns and enforce strict Content-Security-Policy (CSP) rules where possible.
- Utilize endpoint detection and response (EDR) rules that look for HTA execution, suspicious PowerShell usage, and in-memory-only process behaviors.
Incident response best practices:
- Capture and preserve affected WordPress instances and database copies for forensic analysis.
- Trace and catalogue active smart contracts and their on-chain updates for attribution and takedown requests.
- Coordinate disclosures with hosting providers and domain registrars where malicious landing pages are hosted.
Expert Commentary
UNC5142’s shift to on-chain parameterization demonstrates an opportunistic blending of traditional web compromise and Web3 features. By outsourcing mutable metadata to smart contracts, the operator reduces its exposure to static takedown efforts and gains a low-cost, highly available control plane. This represents an important evolutionary step for financially motivated operators and underscores the need for defenders to adapt tooling and monitoring to the nuances of blockchain-enabled abuse.
Outlook
Expect continued experimentation with smart-contract patterns and further operational refinements. Defenders should anticipate that adversaries will adopt similar proxy-like on-chain setups to manage lures, decryption keys, and distribution endpoints. Proactive monitoring of both compromised web properties and relevant blockchain contracts will be required to detect and disrupt these campaigns effectively.
References / Source Attribution
- Google Threat Intelligence Group (GTIG) analysis (summary reporting to industry outlets).
- Guardio Labs — initial EtherHiding disclosure (October 2023).
- Public analyses of ClearFake / ClearShort variants by third-party security firms.