Introduction
The Morris Worm is widely recognized as the first major cyber incident in internet history. Released in November 1988, the worm unintentionally crippled a significant portion of the early internet. What began as an academic experiment quickly escalated into a large-scale outage, permanently altering how organizations viewed system security, network trust, and responsible research.
Background and Historical Context
During the late 1980s, the internet was still in its infancy, largely consisting of academic institutions, government research labs, and defense contractors. Networks such as ARPANET were built on openness and collaboration rather than defense. Authentication mechanisms were weak, systems were rarely patched, and security monitoring was virtually nonexistent.
Within this environment, experimentation was common and largely unrestricted. The Morris Worm emerged from this culture of trust, highlighting how fragile the early internet truly was.
About the Creator
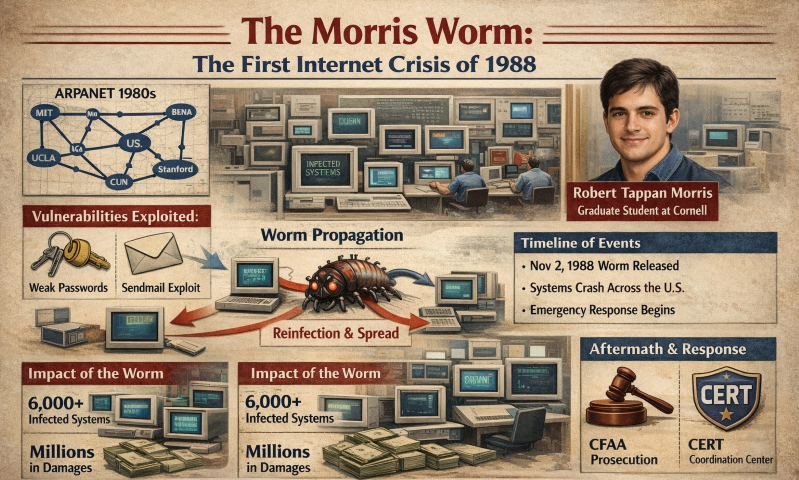
The worm was developed by Robert Tappan Morris, then a graduate student at Cornell University. His intention, as later stated, was to measure the size of the internet by observing how widely the program could propagate. There was no explicit malicious intent, but the lack of safeguards proved catastrophic.
Technical Architecture and Exploitation Methods
The Morris Worm was technically advanced for its time and leveraged multiple attack vectors to ensure propagation:
Exploited Vulnerabilities
- Weak passwords: The worm conducted dictionary-based password guessing against user accounts
- Sendmail debug mode: A misconfigured feature that allowed remote command execution
- Finger daemon buffer overflow: One of the earliest documented real-world buffer overflow exploits
Replication Logic Failure
To avoid easy detection, Morris designed the worm to reinfect systems occasionally, even if it detected an existing copy. However, due to flawed probability logic, reinfection occurred far too frequently. This resulted in exponential process creation, consuming CPU and memory resources until systems became unusable.
Timeline of Events
- November 2, 1988: Worm released from MIT systems to obscure its origin
- Hours later: UNIX machines across the U.S. slow to a crawl or crash entirely
- Same day: Administrators begin disconnecting systems from the network
- Following days: Ad-hoc collaboration among researchers leads to containment strategies
- Weeks later: Post-incident analysis reveals the true scale and cause of the outage
Impact and Scope
At the time of the incident, the internet consisted of approximately 60,000 nodes. The Morris Worm impacted an estimated 10 percent of all connected systems, an unprecedented scale for that era.
Operational Impact
- University research halted for days
- Email and remote access services disrupted
- System administrators forced to take machines offline
Economic Impact
Estimated damages ranged from hundreds of thousands to several million dollars, factoring in downtime, recovery efforts, and lost productivity.
Legal and Policy Consequences
The Morris Worm directly influenced the legal and organizational framework of modern cybersecurity:
- Morris became the first individual prosecuted and convicted under the Computer Fraud and Abuse Act
- Sentenced to probation, community service, and fines
- Prompted the formation of the Computer Emergency Response Team (CERT) Coordination Center
This marked the beginning of formalized incident response and coordinated vulnerability handling.
Industry and Academic Reaction
The incident shattered the assumption that networked systems were inherently safe. It encouraged:
- Development of intrusion detection concepts
- Stronger authentication practices
- Formal security research as an academic discipline
- Increased separation between experimentation and production networks
The Morris Worm is often cited as the event that gave birth to cybersecurity as a profession.
Lessons Learned
Key lessons from the Morris Worm remain relevant today:
- Self-propagating code can cause unintended large-scale damage
- Trust-based networks are inherently risky
- Small logic errors can lead to catastrophic outcomes
- Responsible disclosure and controlled testing environments are essential
Modern Relevance
Despite its age, the Morris Worm shares characteristics with modern malware:
- Automated propagation
- Exploitation of unpatched services
- Abuse of weak credentials
Many ransomware and botnet campaigns today rely on the same fundamental principles demonstrated in 1988.
Conclusion
The Morris Worm was not merely a technical failure but a defining moment in internet history. It forced the global research community to confront the reality that connectivity without security is unsustainable. More than three decades later, the worm’s legacy continues to influence cyber defense strategies, legal frameworks, and ethical standards in computing.
Sources
- FBI.gov – “Morris Worm: 30 Years Since First Major Attack on the Internet”: https://www.fbi.gov/news/stories/morris-worm-30-years-since-first-major-attack-on-internet-110218
- FIRST.org History – Impact on the creation of the CERT coordination model: https://www.first.org/about/history